Log in to API7 Dashboard with SSO
Single Sign-On (SSO) allows users to log in once and access multiple systems without re-entering credentials. It improves efficiency, enhances user experience, and strengthens security by eliminating the need for multiple passwords.
In API7 Enterprise, you can use multiple login options simultaneously. It is possible to create users within API7 while also importing them from other existing systems.
Architecture
Take LDAP as an example:
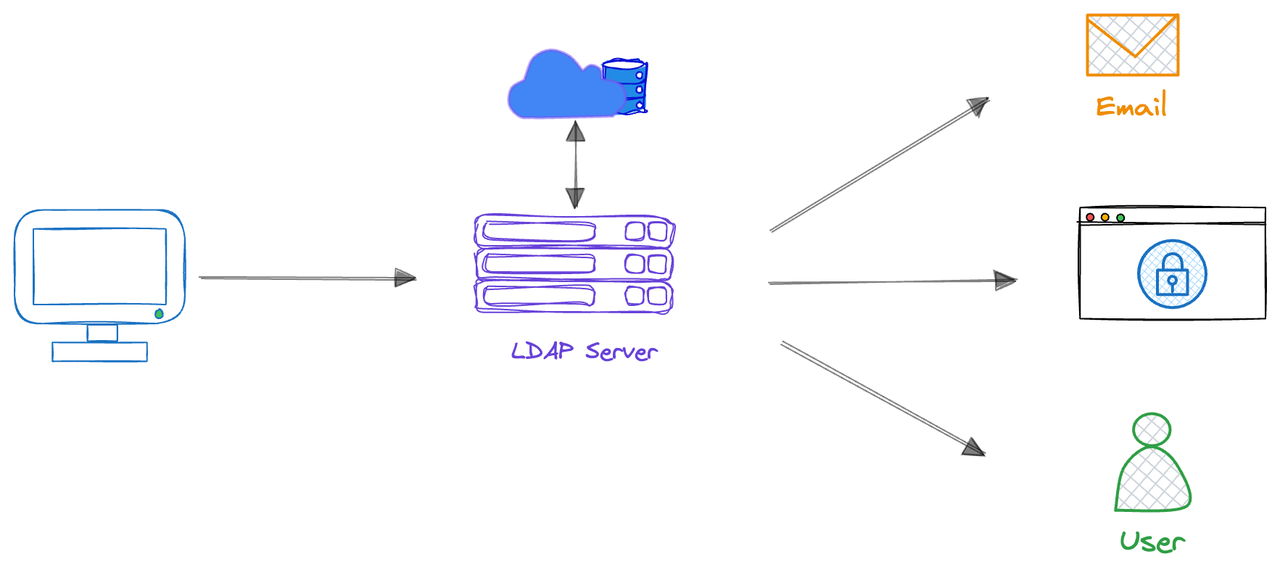
- User Login Request: Users enter their username and password when logging into API7 Enterprise.
- LDAP Verification: API7 Enterprise transfers the credentials provided by the user to the LDAP server for verification.
- Authentication: The LDAP server verifies whether the user's credentials match the user information stored in the LDAP directory.
- Authorization: If verification is successful, the LDAP server returns authorization information to API7 Enterprise, and the system authorizes the user to access corresponding resources based on this information.
- Accessing Resources: Users access API7 Enterprise with the verified identity without having to re-enter credentials.
Prerequisites
- Obtain a user account with Super Admin role.
Integrate with SSO
API7 Enterprise supports Single Sign-On (SSO) with following implementations. Integrating API7 Enterprise with other user systems enables you to log your existing users into API7 Enterprise without signing up for a new API7 account.
- LDAP
- OIDC
- SAML
- Select Organization from the top navigation bar, then choose Settings.
- Click Add Login Option.
- Fill in the Add Login Option form:
- Name: the unique login name, must be identical to users. For example
Employee Account. - Provider: choose
LDAP. - Host: the LDAP host domain. For example,
ldap.example.com. - Port: For example,
1563. - Base Distinguished Name: For example,
oc=users,dc=org,dc=example. - Bind Distinguished Name: the LDAP Bind Distinguished Name (DN) used to perform LDAP search for the user. This LDAP Bind DN should have permissions to search for the user being authenticated. For example,
cn=admin,dc=org,dc=example. - Bind Password: the LDAP bind password used to authenticate with the LDAP server.
- Identifier: the attribute used to identify LDAP users. For example,
cn. - Attributes Mapping: map API7 internal fields to related LDAP attributes to seamlessly integrate and synchronize data.
- Name: the unique login name, must be identical to users. For example
- Click Add.
- Select Organization from the top navigation bar, then choose Settings.
- Click Add Login Option.
- Fill in the Add Login Option form:
- Name: the unique login name, must be identical to users. For example
Employee Account. - Provider: choose
OIDC. - Issuer: the identifier of the OpenID connect provider. For example,
https://accounts.example.com. - Client ID: the unique identifier of your application, assigned by the OIDC provider. For example,
API7. - Client Secret: secret key used for authentication, assigned by the OIDC provider.
- Request Scope: Access tokens often possess different scopes, which limit their usage. For example,
profile,email. - Root URL: the URL used to access API7 for generating callback URL. For example,
https://auth.example.com/oidc. - SSL verify: default value is open.
- Name: the unique login name, must be identical to users. For example
- Click Add.
- Select Organization from the top navigation bar, then choose Settings.
- Click Add Login Option.
- Fill in the Add Login Option form:
- Name: the unique login name, must be identical to users. For example
Employee Account. - Provider: choose
SAML. - Identity Provider Metadata URL: URL used to obtain information about the Identity Provider, such as its public key, supported SAML versions, signature algorithms, etc. For example,
https://idp.example.com/metadata. - Service Provider Root URL: the entity that requests authentication and authorization from the Identity Provider (IdP).For example,
https://sp.example.com. - Entity ID: a unique identifier for the Service Provider (SP) or Identity Provider (IdP) entity. It typically serves as a globally unique identifier for the entity within the SAML federation. For example,
https://sp.example.com/saml/metadata.
- Name: the unique login name, must be identical to users. For example
- Click Add.
Login with SSO
Once you have configured the Login Options, external users will be able to directly log in to the API7 Dashboard without the need for signing up.
- Visit the API7 Dashboard at
http://localhost:7080. - Choose from the login option name, for example Login with Employee Account.
- Enter your username and password.
- Click Login.
Delete Imported Users
If you delete a user with SSO login options in Users, it only means that the user will lose all their roles. However, they can still log in to the API7 Dashboard as a new user. To completely block their access to the API7 Dashboard, you must delete them from the original system.
Assign Roles for Imported Users
All newly imported users will be assigned the Viewer role by default until the Super Admin assigns them different roles.
Delete a Login Option
Deleting a login option will result in the removal of all users associated with it.
- Select Organization from the top navigation bar, then choose Users.
- Check if there are any users still using this login option. If yes, notify them first.
- Select Organization from the top navigation bar, then choose Settings.
- Click Delete of the target login option.
- Double confirm.